There are no items in your cart
Add More
Add More
| Item Details | Price | ||
|---|---|---|---|
The NIST Risk Management Framework (RMF) is a widely recognized cybersecurity framework used by government agencies and private enterprises to manage information system risks through a structured 6-step process.
To address the growing use and complexity of artificial intelligence, NIST also developed a separate framework, the NIST AI Risk Management Framework (AI RMF). While both frameworks are grounded in a risk-based philosophy, the AI RMF is tailored specifically to ensure trustworthy, responsible, and ethical AI systems. It focuses on four key functions: Govern, Map, Measure, and Manage.
In this guide, we’ll explore the 6 Steps of the NIST RMF with real-world examples.
The NIST Risk Management Framework (RMF), developed by the National Institute of Standards and Technology (NIST), is a comprehensive methodology designed to embed security, privacy, and risk management into the lifecycle of information systems.
It offers a standardized, repeatable process that guides organizations through the identification, assessment, and mitigation of cybersecurity risks. While originally developed for U.S. federal agencies, the RMF has gained widespread adoption across private sector institutions seeking robust cybersecurity governance, regulatory compliance, and operational resilience.
Read more on What is Risk Management in Banks here!
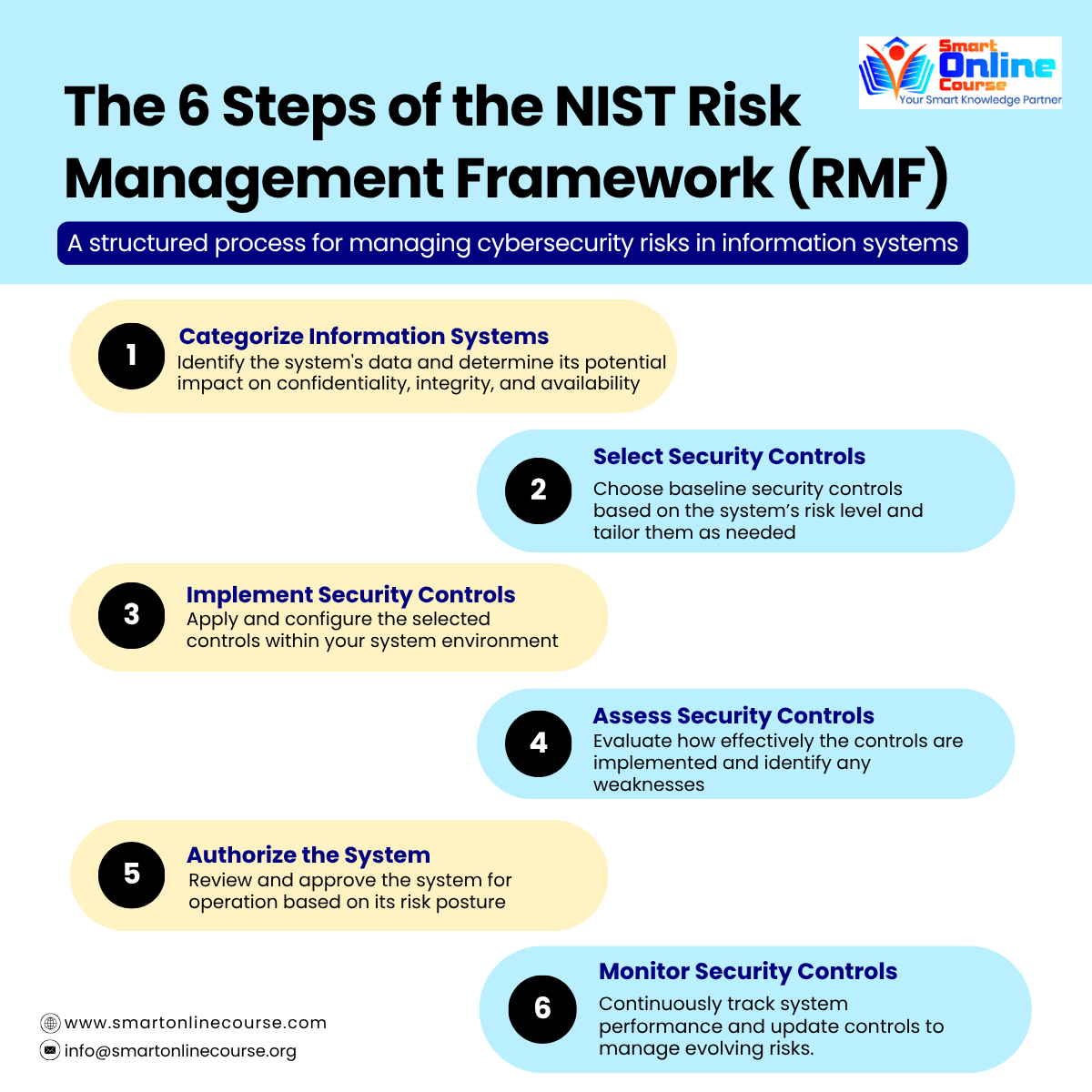
The NIST RMF outlines a six-step process that helps organizations integrate cybersecurity and risk management into system development and operations. Below, we break down each step with real-world examples.
1. Categorize Information Systems
This foundational step defines what needs protection. Organizations assess their information systems based on the potential impact of a security breach, specifically its effect on confidentiality, integrity, and availability (the CIA triad).
Example: A bank categorizes its customer database as high impact, while its internal HR system might be considered moderate.
Reference: FIPS 199 and NIST SP 800-60.
Based on the system’s impact level, appropriate security controls are selected from NIST SP 800-53. These controls are then tailored to align with the system’s mission, environment, and operational needs.
Example: A healthcare provider selects encryption, access controls, and audit logging to protect electronic health records (PHI).
Output: A System Security Plan (SSP) that documents selected and tailored controls.
Chosen controls are implemented within the system's architecture. This includes technical measures (e.g., firewalls, MFA) and administrative processes (e.g., policies, staff training).
Example: A fintech company configures MFA for all user logins and automates daily system backups.
Outcome: Controls are deployed, documented, and traceable.
The effectiveness of the implemented controls is evaluated by independent assessors. This includes testing, document review, and verification of compliance with baseline requirements using NIST SP 800-53A.
Example: A cybersecurity auditor tests an incident response system and confirms that encryption keys are rotated regularly.
Output: A Security Assessment Report (SAR) that identifies strengths, weaknesses, and residual risk.
An Authorizing Official (AO) reviews the assessment results and determines whether the system meets the organization’s acceptable risk threshold. If so, an Authorization to Operate (ATO) is granted.
Example: A government agency grants ATO for a cloud-based application after confirming all required moderate-impact controls are implemented.
Outcome: Formal approval for the system to operate in production.
Risk management is a continuous process. Organizations must monitor control performance, detect new vulnerabilities, and respond to evolving threats. This includes updating documentation and reassessing risk regularly.
Example: A financial institution uses a SIEM platform to monitor login activity, detect anomalies, and generate quarterly risk reports.
Output: Updated risk documentation and continuous authorization support.
While the original NIST RMF was developed to secure federal information systems, its structured, risk-based approach has paved the way for newer frameworks like the NIST AI Risk Management Framework (AI RMF), designed specifically for managing risks associated with artificial intelligence.
The NIST AI RMF builds on the foundational principles of the RMF but adapts them for AI’s unique challenges, such as algorithmic bias, lack of transparency, and model drift. It introduces four core functions, Govern, Map, Measure, and Manage, which mirror the lifecycle-based approach of RMF, focusing on ensuring that AI systems are trustworthy, ethical, and aligned with human values.
Want to learn more about NIST AI RMF, it's principles, structure, and application, with real-world case studies?
Enroll today in our 9-hour professional certification course - Responsible AI Risk Management using the NIST AI Framework and learn to build AI systems that are ethical, explainable, and compliant with global standards.